
How to Revoke Certificate in ADCS
In this age of ever-evolving methods of securing our information, one of the unsung heroes of cybersecurity is digital certificates. Though they may not be widely known about, they’re a powerful tool in making sure our data stays confidential. Therefore, having a fundamental understanding of how to manage certificates, and especially how to revoke a certificate, is now more important than ever.
But what happens when a certificate needs to be invalidated, whether it’s something as simple as employee termination, or something more complex like a compromised certificate authority? Do you know how to revoke a certificate though Active Directory Certificate Services (ADCS)? In this blog, we’ll help demystify the task of certificate revocation. By the end, you’ll have a clearer understanding of how exactly to revoke a certificate using ADCS, and to prevent interruptions within your organization.
Reasons for Revocation
Certificate revocation is the act of invalidating a certificate before its scheduled expiration date. Certificates that have been revoked are stored on a list by the CA, known as the Certificate Revocation List (CRL). When a client attempts to initiate a connection with a server, it checks for issues with the certificate, and part of this check is to ensure that the certificate is not listed on the CRL. The process of how to revoke certificate may seem confusing, but by reading the blog, you will gain a better understanding of how to do it.
There are several reasons an admin may need to revoke a certificate. The most common reasons will usually involve when a user gets terminated / leaves the company, however there are many scenarios in which a certificate should be revoked:
- Employee termination
- The legal name of an employee has changed
- Computer is lost or stolen
- The CA certificate gets compromised
- The CA is being replaced with a new one and all issued certificates need to be replaced
NOTE: Disabling a user or a computer object in AD UC does NOT automatically revoke the associated certificate! Certificate revocation is a manual process that should be added into your employee termination or device “offboarding” checklist.
Revocation Procedure
On the issuing CA that the certificate was issued from, launch the Certificate Authority tool in Server Manager.
Click on “Issued Certificates”
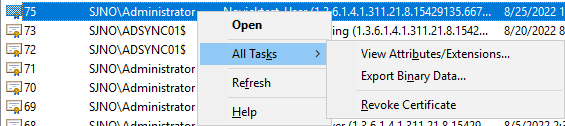
Scroll through the list of certificates and located the certificate you wish to revoke.
Right click on the certificate > All Tasks > Revoke Certificate
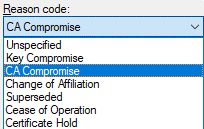
Select the reason that best suits your needs and click “Yes”
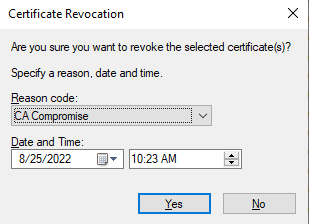
You will now see the certificate in the “Revoked Certificates”
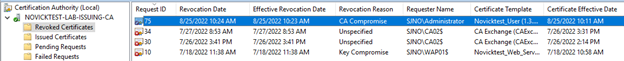
Publishing New CRL
After the certificate has been revoked, the final step is to Publish (or update) a new CRL. Any device or application performing CRL checking will not be aware of how to revoke a certificate until it has been added to the CRL file that the application is checking against.
CRL publishing should occur automatically, based on the publishing intervals configured on the CA. However, in some cases, you may not want to wait for automatic publishing to occur, and instead publish a new CRL immediately.
To check the configured publishing intervals on the CA:
In Certification Authority management on the CA, right-click on “Revoked Certificates”
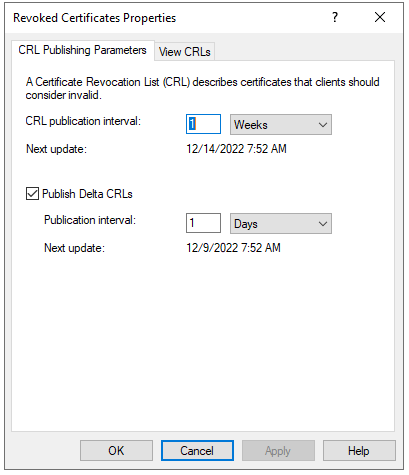
The CRL Publishing intervals, as well as the time when the next automatic publishing will occur, will be shown here:
To manually publish an updated CRL file on demand:
In Certification Authority management on the CA, right-click on “Revoked Certificates” > All Tasks > Publish
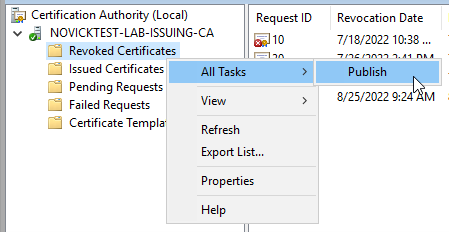
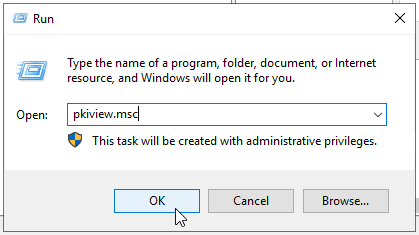
To verify that publishing succeeded:
On your CA Server, launch “pkiview.msc” from a Run dialog box
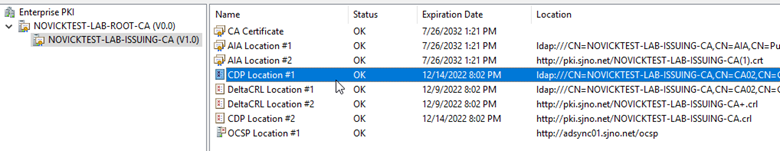
Once pkiview.msc launches (also known as “Enterprise PKI”), verify that the expiration dates on the “CDP Locations” and/or “DeltaCRL Locations” has been updated accordingly
OTHER BLOGS:


How to Clean and Compact the ADCS Database

How to Revoke Certificate in ADCS

Wildcard Certificates 101


