CA Event Auditing and Monitoring
In today’s fast-paced landscape of digital operations, where data is both a lifeline and a potential vulnerability, the importance of efficient event monitoring and auditing cannot be understated. CA Event Auditing and Monitoring is a critical component for organizations striving towards data security and compliance. In this blog, we will discuss the intricacies of CA technologies, shedding light on how they contribute to identification, tracking, and analysis of events within an IT environment. As we progress, we’ll showcase the all-important role that CA Event Auditing and Monitoring plays in fortifying the foundations of cybersecurity, help you get your own CA auditing up and running, and ultimately safeguarding the integrity of your digital assets.
Enabling CA Event Auditing
In order for ADCS to log events to Event Viewer, Auditing must be enabled/configured in BOTH of the following places:
- At the CA level (within ADCS itself)
- At the OS level (in Windows Object Access Auditing settings)
To Enable at the CA Level
The first step to enabling CA Event Monitoring is on the Certificate Authority itself. This can be configured via “certutil” command, or via the Certification Authority MMC (certsrv.msc)
Via Certutil command:
Use this command to set the audit filter:
Certutil -setreg CA\AuditFilter 127
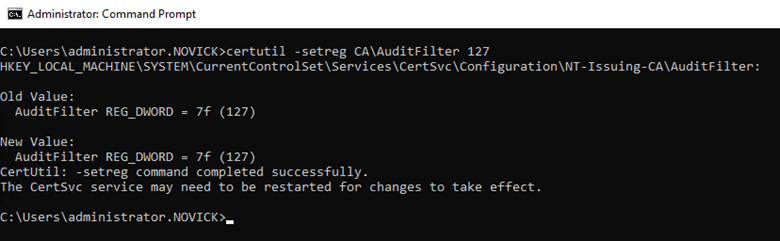
Use this command to verify the current audit filter settings:
Certutil -getreg CA\Auditfilter
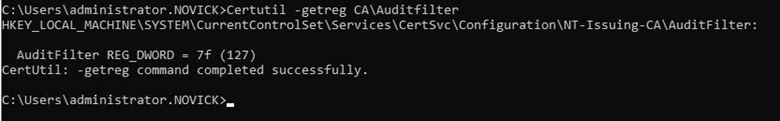
Via Certification Authority MMC (certsrv.msc):
Right-click on the CA > Properties
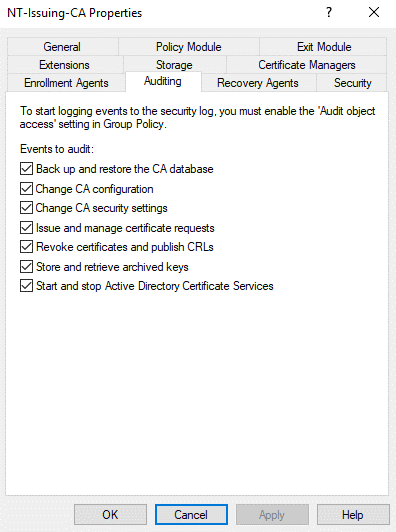
In the Properties window that appears, click on the “Auditing” tab and check all checkboxes under “Events to audit:” then click OK
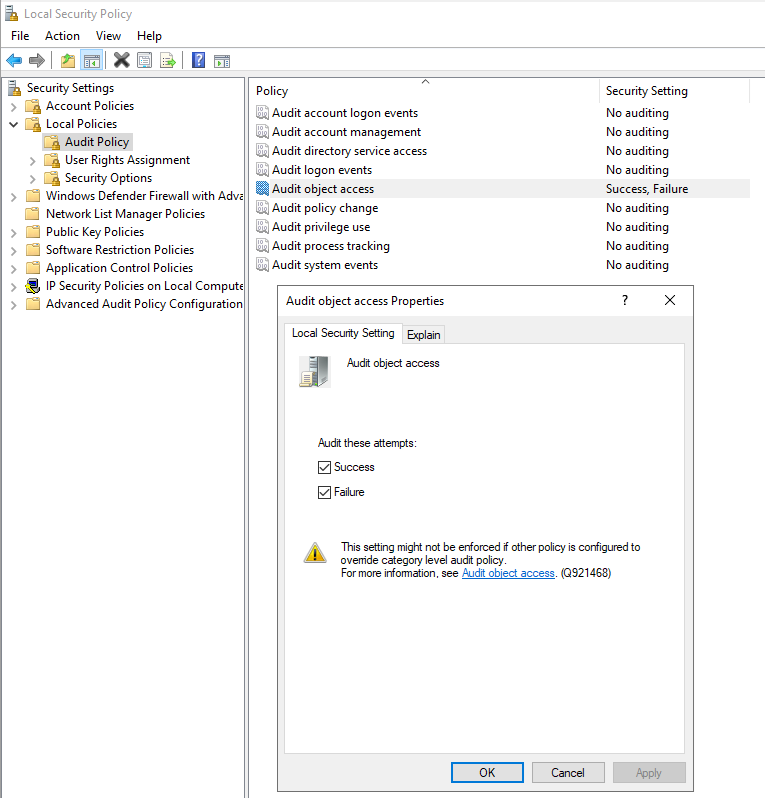
To Enable at the OS Level
In order to ensure CA Event Auditing is working as intended, it must be enabled at the OS level as well. This can be accomplished via GPO applied to the CA server, or alternatively via Local Security Policy (secpol.msc) on the CA server itself. It is strongly recommended to use GPO method so that we can be confident that the settings stick and are not overwritten later by another GPO.
Via GPO:
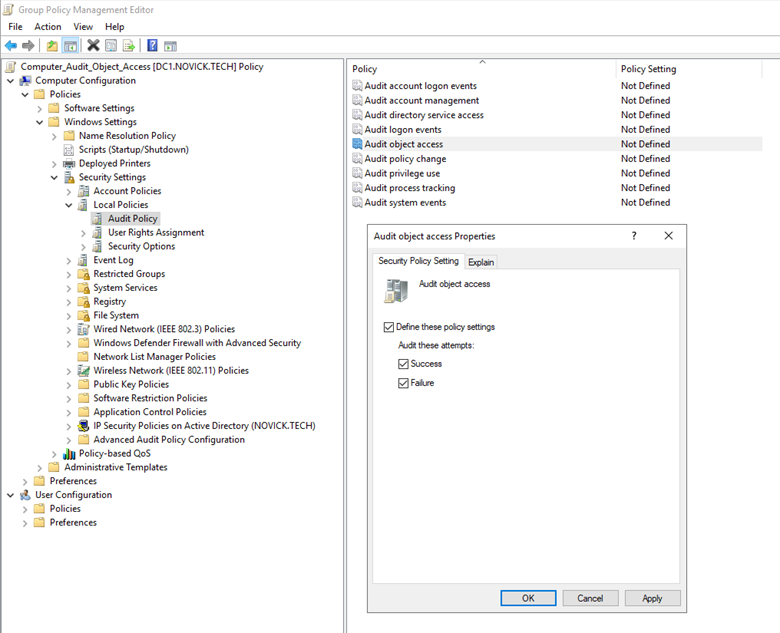
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy > “Audit object access”
Check the boxes for both “Success” and “Failure”
This can be accomplished via GPO applied to the CA server, or alternatively via Local Security Policy (secpol.msc) on the CA server itself. It is strongly recommended to use GPO method so that we can be confident that the settings stick and are not overwritten later by another GPO.
Via GPO:
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy > “Audit object access”
Check the boxes for both “Success” and “Failure”
Windows Security Logs
The following tables provide a full list of events generated by Active Directory® Certificate Services CA role, along with recommendations for which events should be monitored.
The “Current Windows Event ID” column lists the current event ID as it is implemented in versions of Microsoft Windows Server® that are currently in mainstream support. The “Potential Criticality” column identifies whether the event should be considered low, medium or high criticality in detecting attacks. The event summary contains a brief description of the event.
In the Event Viewer on your Issuing CA, you can go to Windows Logs > Security and find the following Event IDs below:
Current Windows Event ID | Potential Criticality | Event Summary | Audit Filter Required | Description |
4868 | Low | The certificate manager denied a pending certificate request. Request ID: %1 | Issue and manage certificate requests |
|
4869 | Low | Certificate Services received a resubmitted certificate request. Request ID: %1 | Issue and manage certificate requests |
|
4870 | Low | Certificate Services revoked a certificate. Serial Number: %1 Reason: %2 | Revoke certificates and publish CRLs |
|
4871 | Low | Certificate Services received a request to publish the certificate revocation list (CRL). Next Update: %1 Publish Base: %2 Publish Delta: %3 | Revoke certificates and publish CRLs |
|
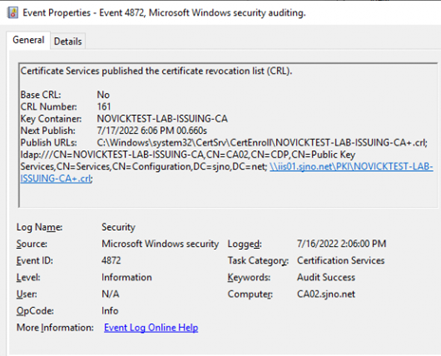
4872 | Low | Certificate Services published the certificate revocation list (CRL). Base CRL: %1 CRL Number: %2 Key Container: %3 Next Publish: %4 Publish URLs: %5 | Revoke certificates and publish CRL |
|
4873 | Medium | A certificate request extension changed. Request ID: %1 Name: %2 Type: %3 Flags: %4 Data: %5 | Issue and manage certificate requests | If this functionality is not used by the CA, it may indicate tampering with a request |
4874 | Medium | One or more certificate request attributes changed. Request ID: %1 Attributes: %2 | Issue and manage certificate requests | If this functionality is not used by the CA, it may indicate tampering with a request |
4875 | Low | Certificate Services received a request to shut down. | Start and stop Active Directory® Certificate Services | This event is triggered when the certutil –shutdown command is issued to the CA |
4876 | Low | Certificate Services backup started. Backup Type: %1 | Back up and restore the CA database |
|
4877 | Low | Certificate Services backup completed. | Back up and restore the CA database |
|
4878 | Low | Certificate Services restore started. | Back up and restore the CA database |
|
4879 | Low | Certificate Services restore completed. | Back up and restore the CA database |
|
4880 | Low | Certificate Services started. Certificate Database Hash: %1 Private Key Usage Count: %2 CA Certificate Hash: %3 CA Public Key Hash: %4 | Start and stop Active Directory® Certificate Services |
|
4881 | Low | Certificate Services stopped. Certificate Database Hash: %1 Private Key Usage Count: %2 CA Certificate Hash: %3 CA Public Key Hash: %4 | Start and stop Active Directory® Certificate Services |
|
4882 | High | The security permissions for Certificate Services changed. %1 | Change CA security settings | May indicate an attacker granting permissions for other accounts to enroll. |
4883 | Medium | Certificate Services retrieved an archived key. Request ID: %1 | Store and retrieve archived keys |
|
4884 | Low | Certificate Services imported a certificate into its database. Certificate: %1 Request ID: %2 | Issue and manage certificate requests |
|
4885 | High | The audit filter for Certificate Services changed. Filter: %1 | Change CA security settings | May indicate an attacker disabling monitoring in an attempt to cover their tracks prior to certificate activities. |
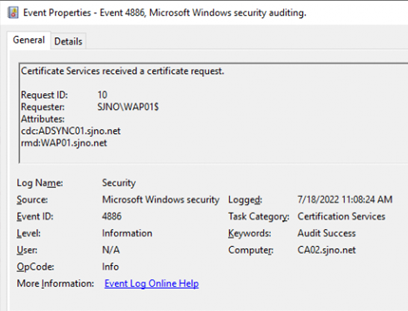
4886 | Low | Certificate Services received a certificate request. Request ID: %1 Requester: %2 Attributes: %3 | Issue and manage certificate requests |
|
4887 | Medium | Certificate Services approved a certificate request and issued a certificate. Request ID: %1 Requester: %2 Attributes: %3 Disposition: %4 SKI: %5 Subject: %6 | Issue and manage certificate requests | Issuance of certificates that contain usages that allow the owner to perform privileged operations (Enrollment Agent, Code Signing etc.) or certificates issued to VIP users should be monitored. |
4888 | Medium | Certificate Services denied a certificate request. Request ID: %1 Requester: %2 Attributes: %3 Disposition: %4 SKI: %5 Subject: %6 | Issue and manage certificate requests |
|
4889 | Low | Certificate Services set the status of a certificate request to pending. Request ID: %1 Requester: %2 Attributes: %3 Disposition: %4 SKI: %5 Subject: %6 | Issue and manage certificate requests |
|
4890 | High | The certificate manager settings for Certificate Services changed. Enable: %1 %2 | Change CA security settings | May indicate tampering with permissions with what users are able to enroll on behalf of other users, commonly used to issue smart card certificates. |
4891 | Medium | A configuration entry changed in Certificate Services. Node: %1 Entry: %2 Value: %3 | Change CA configuration | Can be used to monitor for changes to Policy/Exit modules on the CA or configuration of CDP/AIA extensions. |
4892 | Medium | A property of Certificate Services changed. Property: %1 Index: %2 Type: %3 Value: %4 | Change CA configuration | Can be used to track changes to Key Recovery Agent configuration |
4893 | Low | Certificate Services archived a key. Request ID: %1 Requester: %2 KRA Hashes: %3 | Store and retrieve archived keys |
|
4894 | Low | Certificate Services imported and archived a key. Request ID: %1 | Store and retrieve archived keys |
|
4895 | Low | Certificate Services published the CA certificate to Active Directory® Domain Services. Certificate Hash: %1 Valid From: %2 Valid To: %3 |
|
|
4896 | High | One or more rows have been deleted from the certificate database. Table ID: %1 Filter: %2 Rows Deleted: %3 | Issue and manage certificate requests | May indicate an attacker covering their tracks after issuing certificates. |
4897 | Medium | Role separation enabled: %1 | Change CA security settings | If role separation is used, this can be used to trigger an alert if the expected configuration changes. |
4898 | Medium | Certificate Services loaded a template. %1 v%2 (Schema V%3) %4 %5 Template Information: Template Content: %7 Security Descriptor: %8 Additional Information: Domain Controller: %6 | Change CA security settings | Alert if templates that are not expected on a CA are loaded. |
4899 | Medium | A Certificate Services template was updated. %1 v%2 (Schema V%3) %4 %5 Template Change Information: Old Template Content: %8 New Template Content: %7 Additional Information: Domain Controller: %6 | Change CA security settings |
|
4900 | Medium | Certificate Services template security was updated. %1 v%2 (Schema V%3) %4 %5 Template Change Information: Old Template Content: %9 New Template Content: %7 Old Security Descriptor: %10 New Security Descriptor: %8 Additional Information: Domain Controller: %6 | Change CA security settings |
|
Examples from Event Viewer
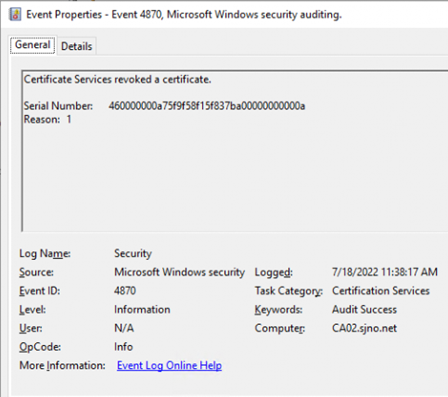
Event 4870 - Certificate Revocation
Event 4872 – CRL Publishing
Event 4886 - Certificate Request via MMC
Event 4887 - Certificate Services approved a certificate request and issued a certificate


